Part two Securing, observing,and controlling your service’s network traffic
Chapter 4 Istio gateways: Getting traffic into a cluster
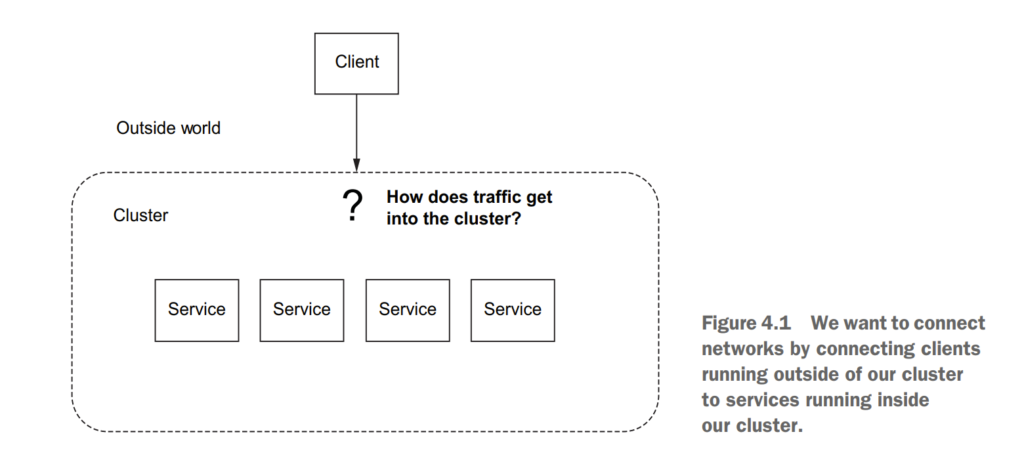
4.1 Traffic ingress concepts
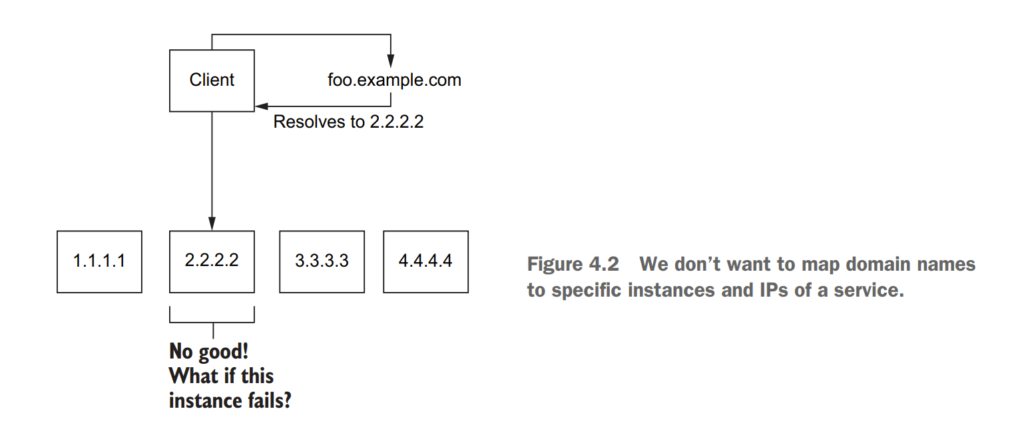
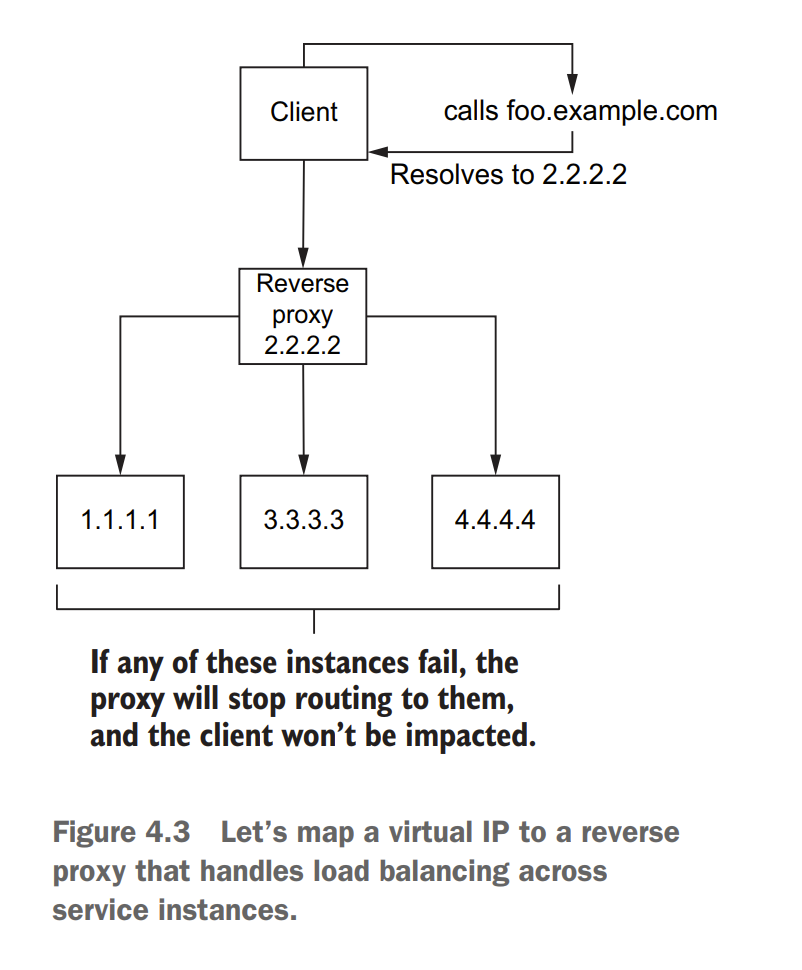
4.1.1 Virtual IPs: Simplifying service access
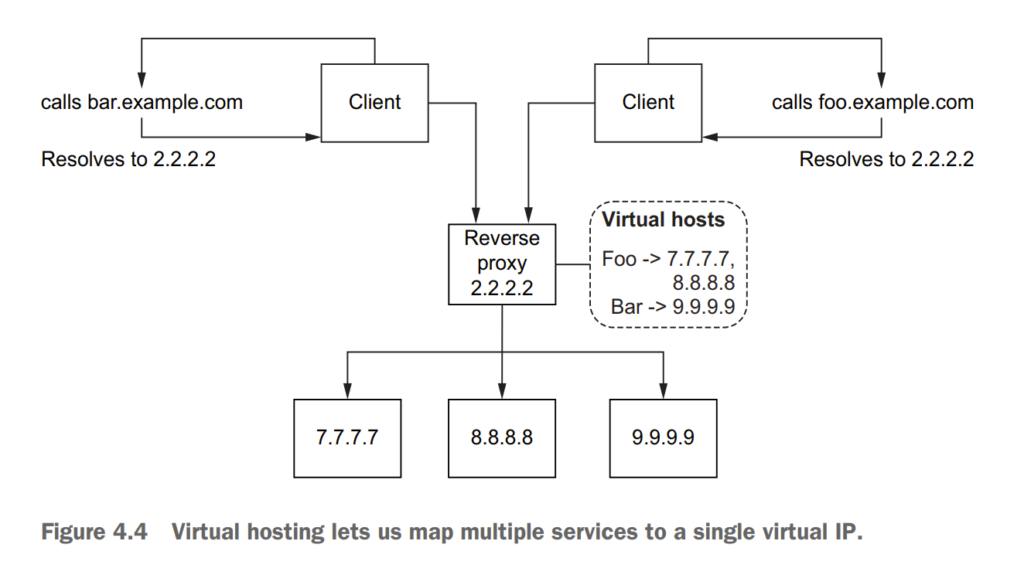
4.1.2 Virtual hosting: Multiple services from a single access point
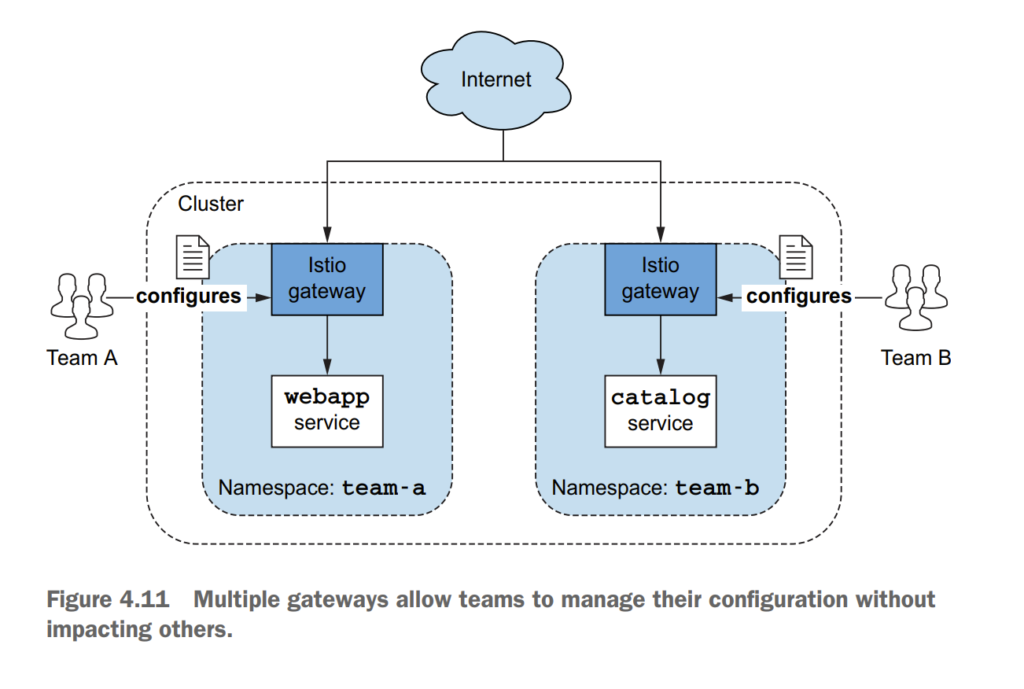
4.2 Istio ingress gateways
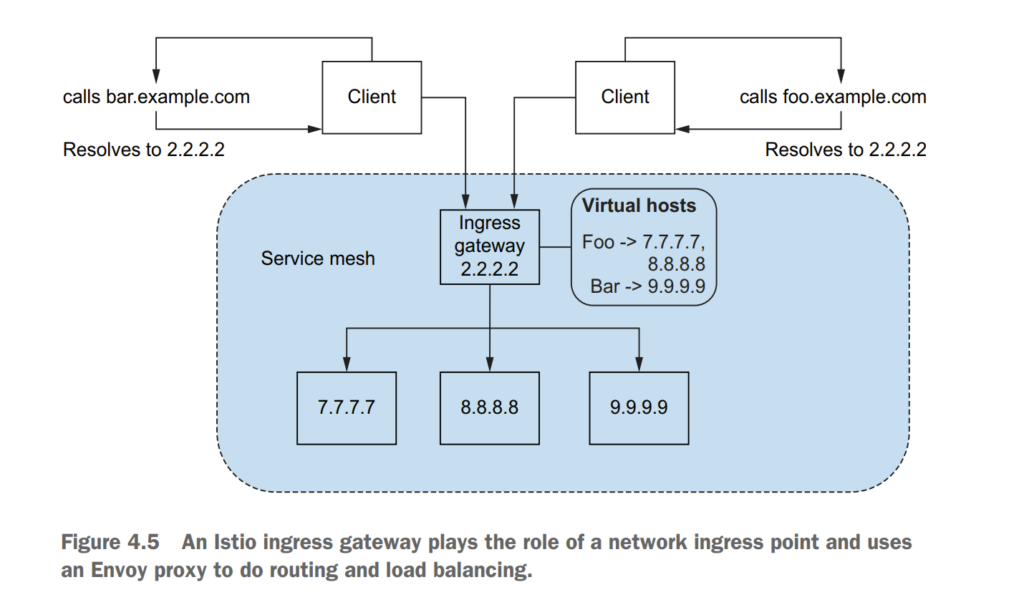
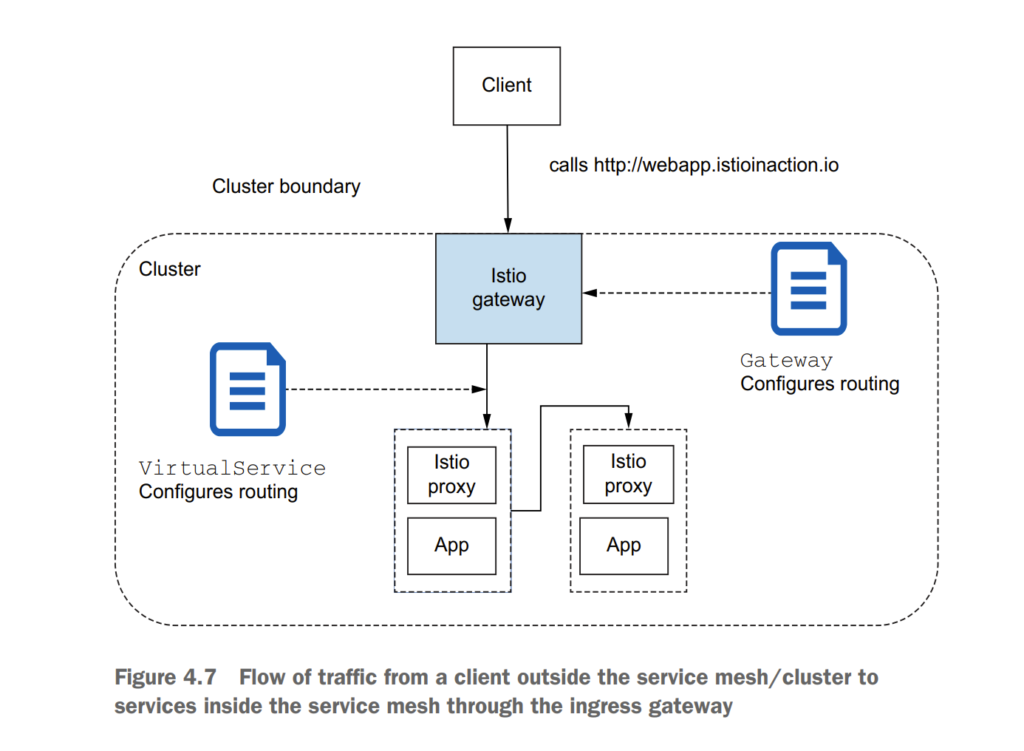
4.2.3 Overall view of traffic flow
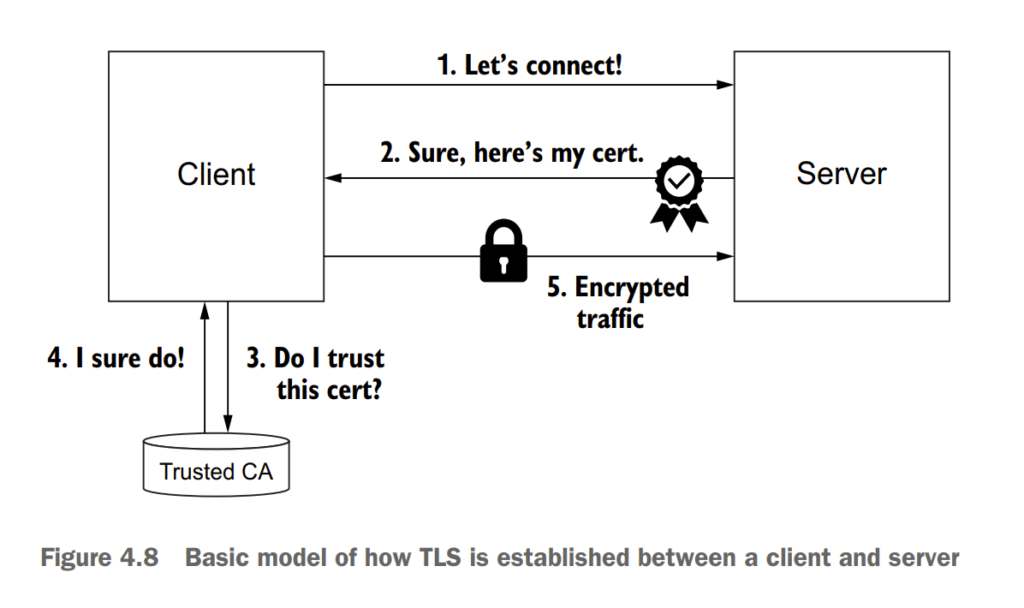
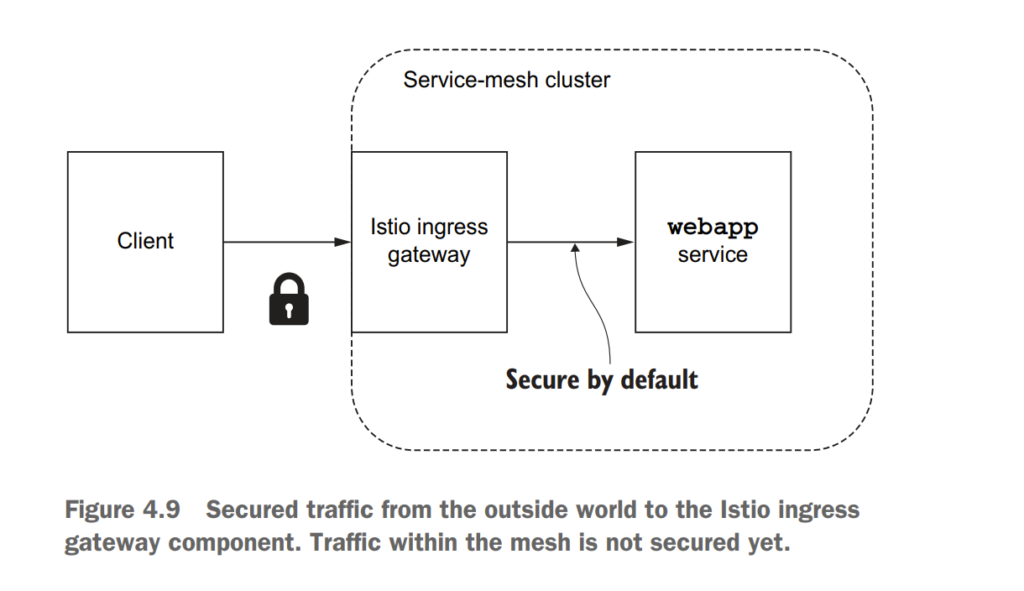
4.3 Securing gateway traffic
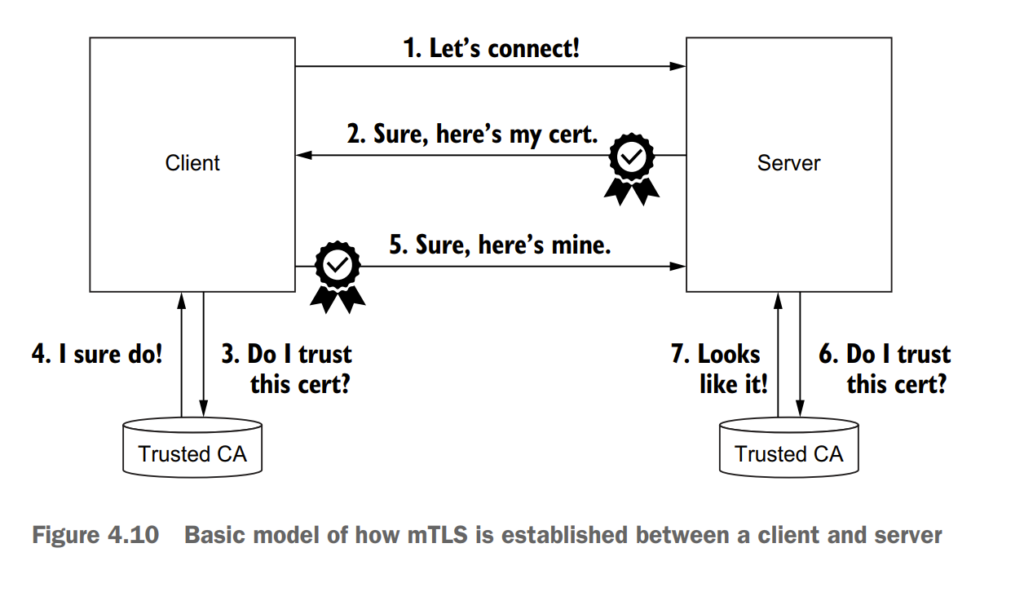
4.3.3 HTTP traffic with mutual TLS
4.5 Operational tips
Chapter 5 Traffic control: Fine-grained traffic routing
5.1 Reducing the risk of deploying new code
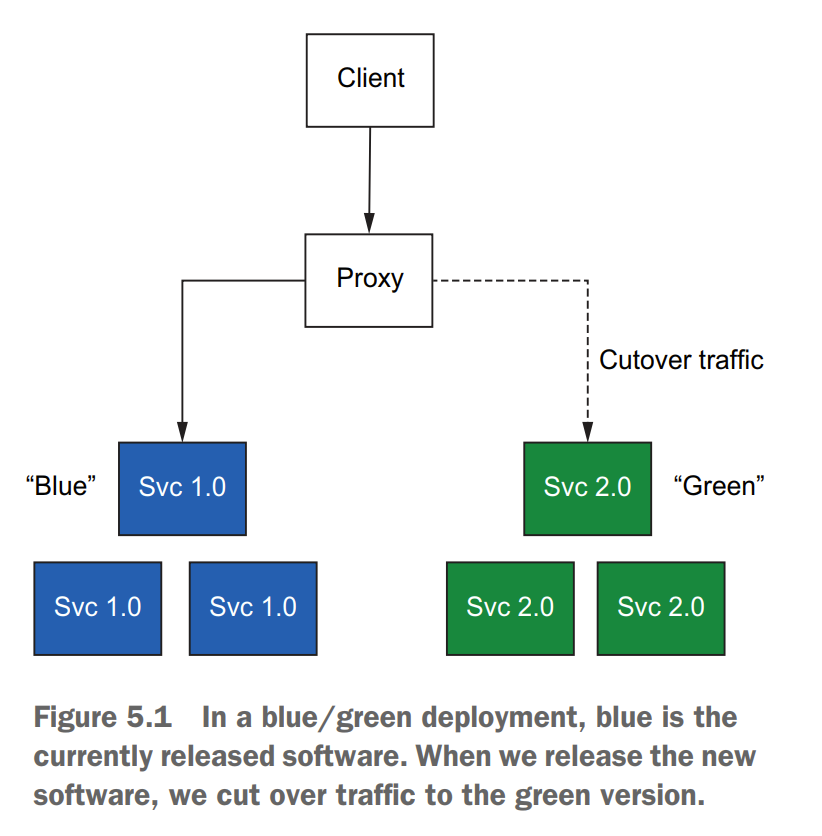
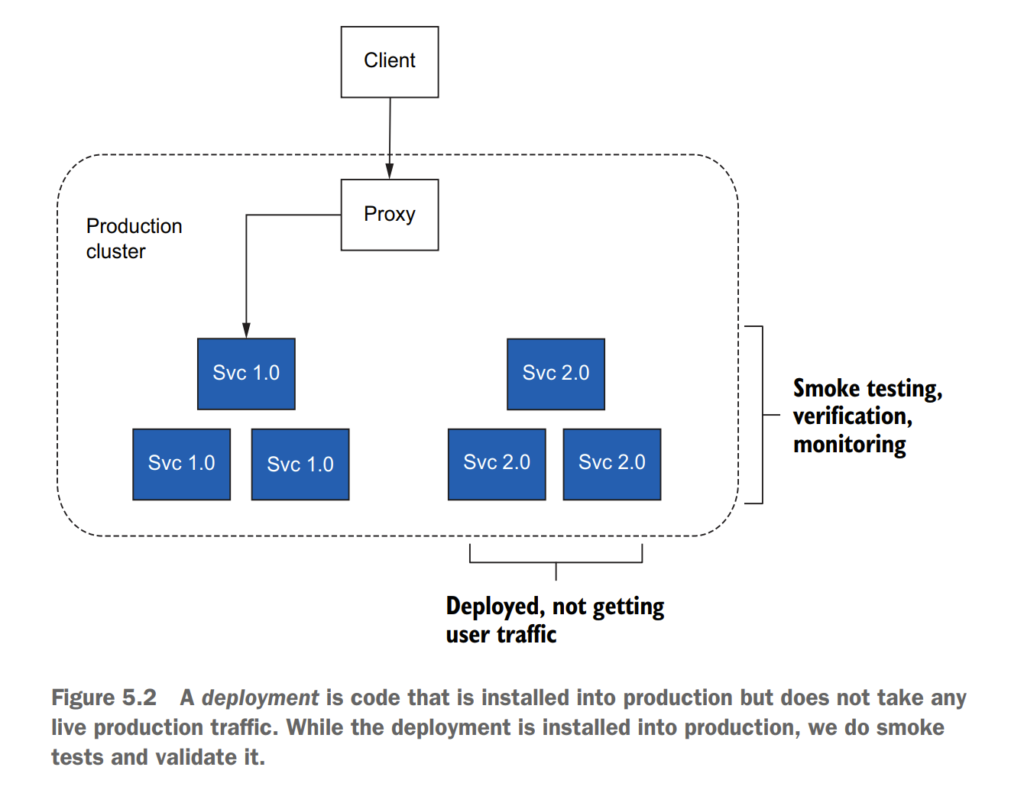
5.1.1 Deployment vs. release
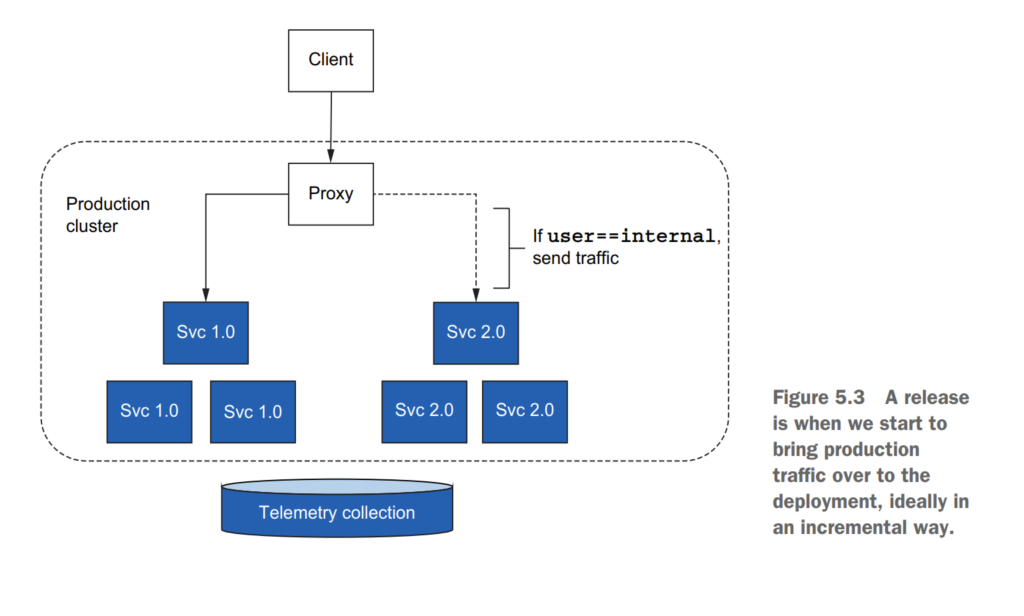
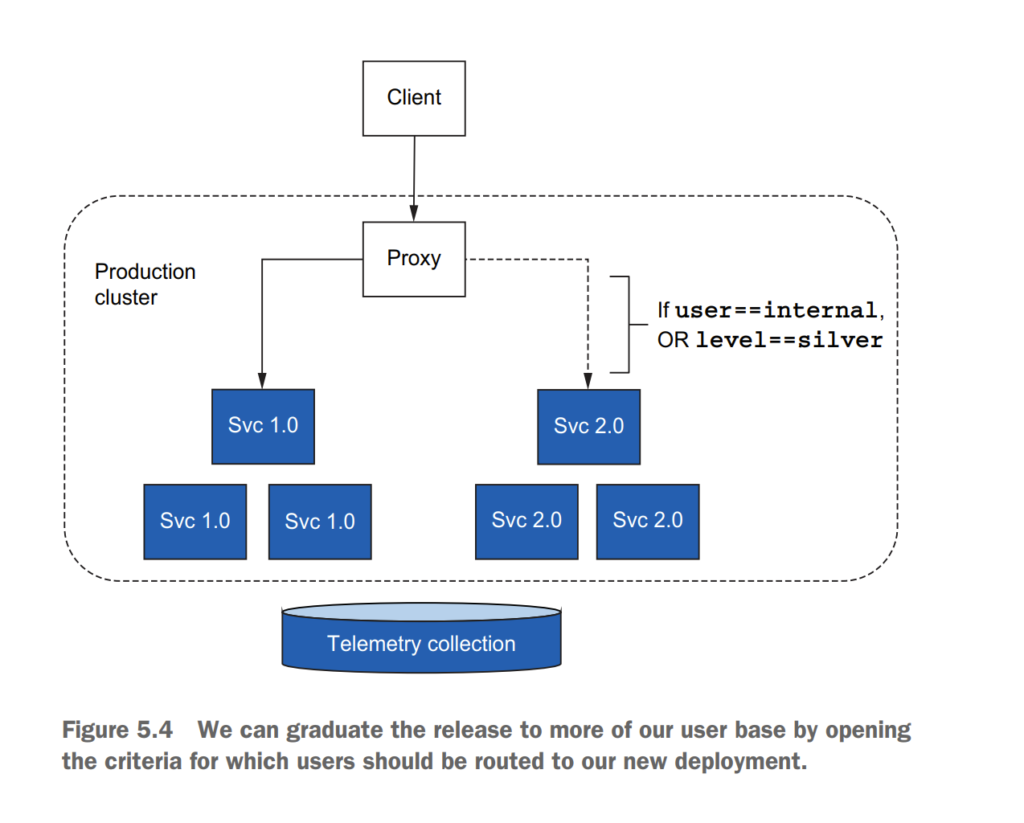
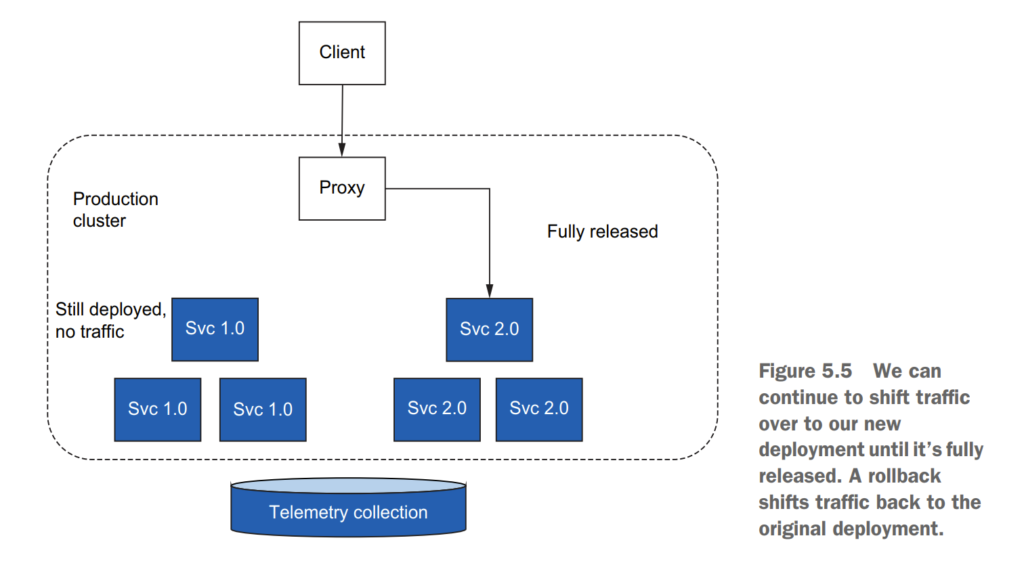
5.2 Routing requests with Istio
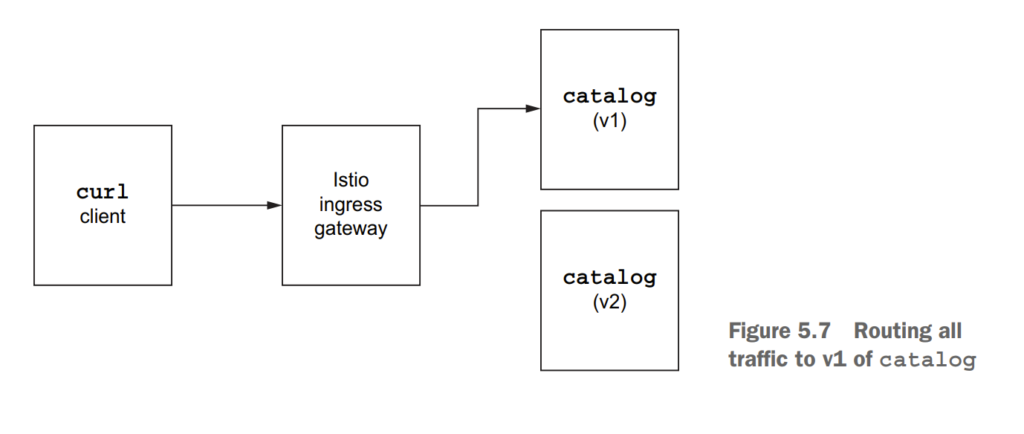
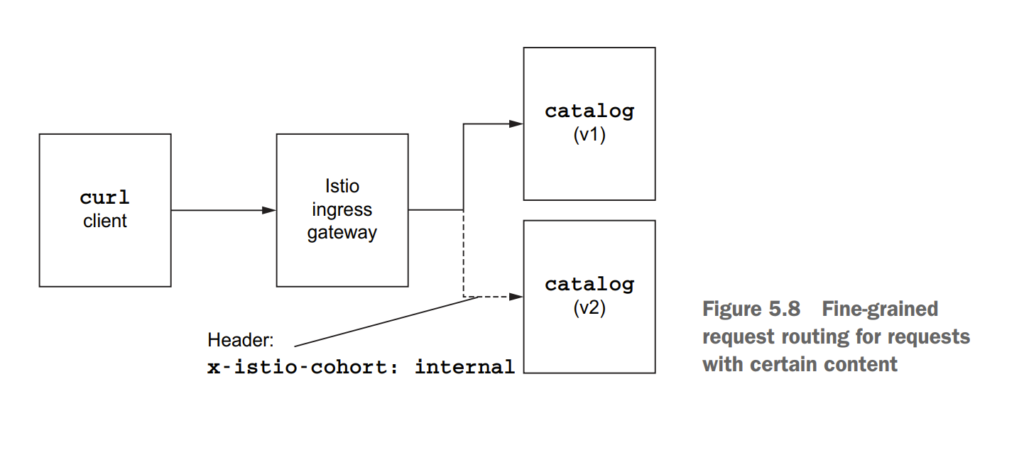
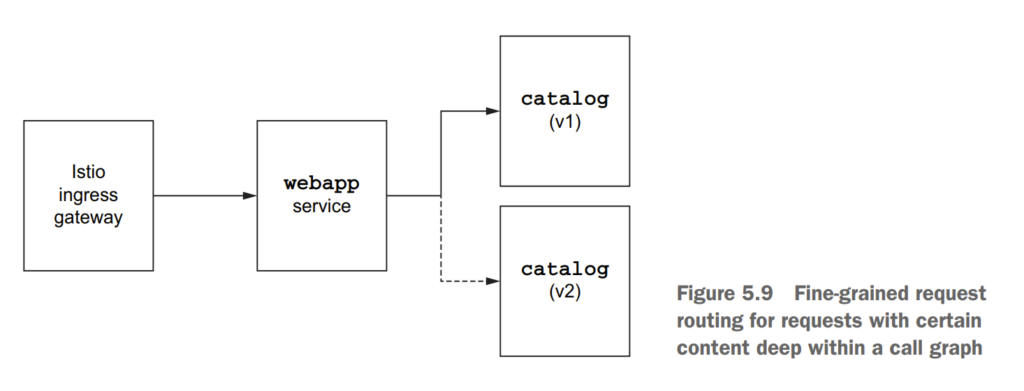
5.3 Traffic shifting
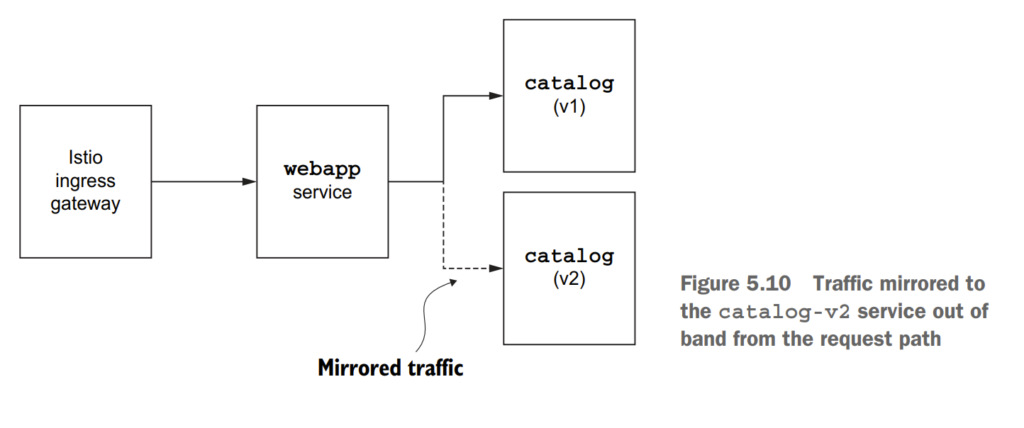
5.4 Reducing risk even further: Traffic mirroring
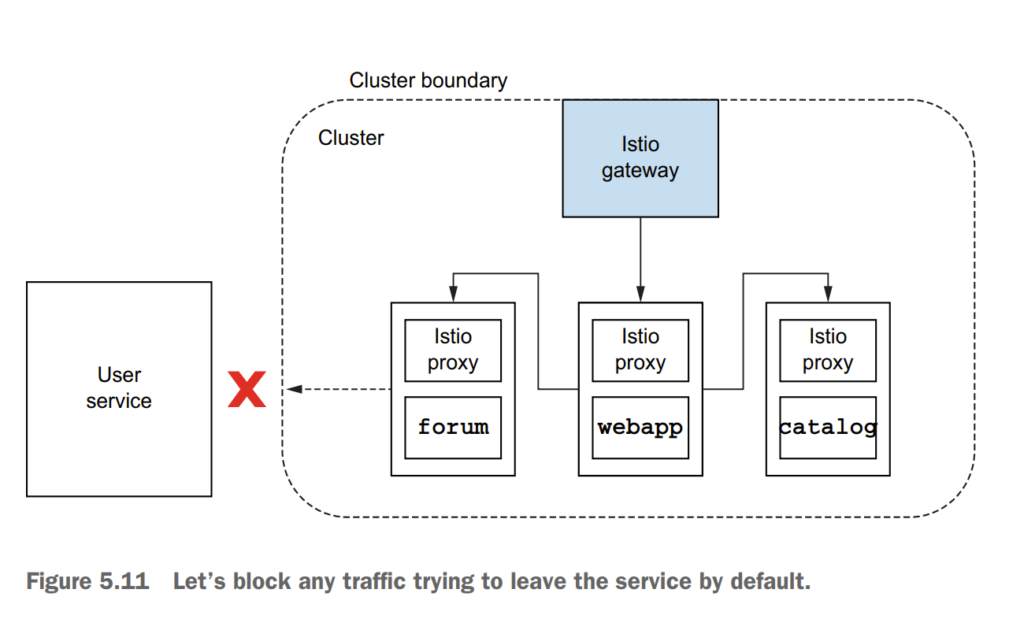
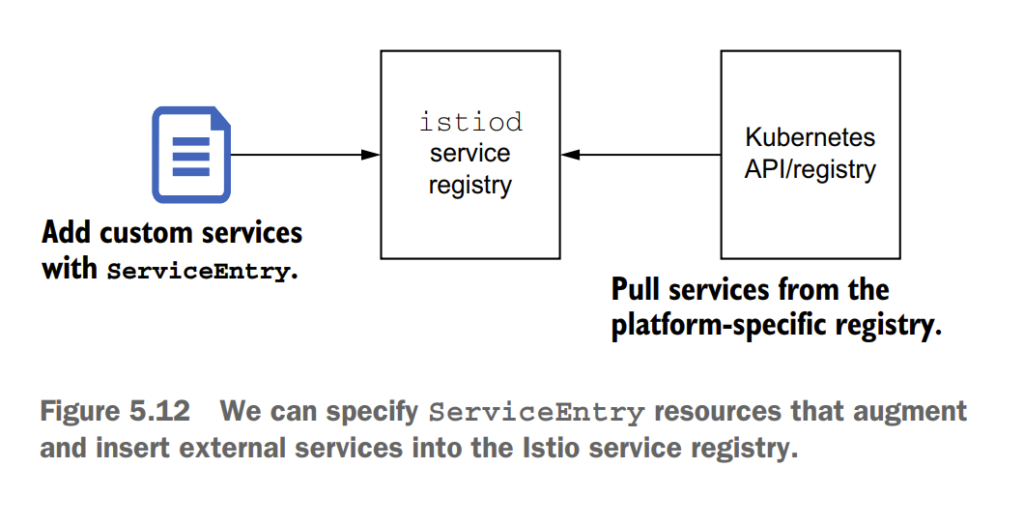
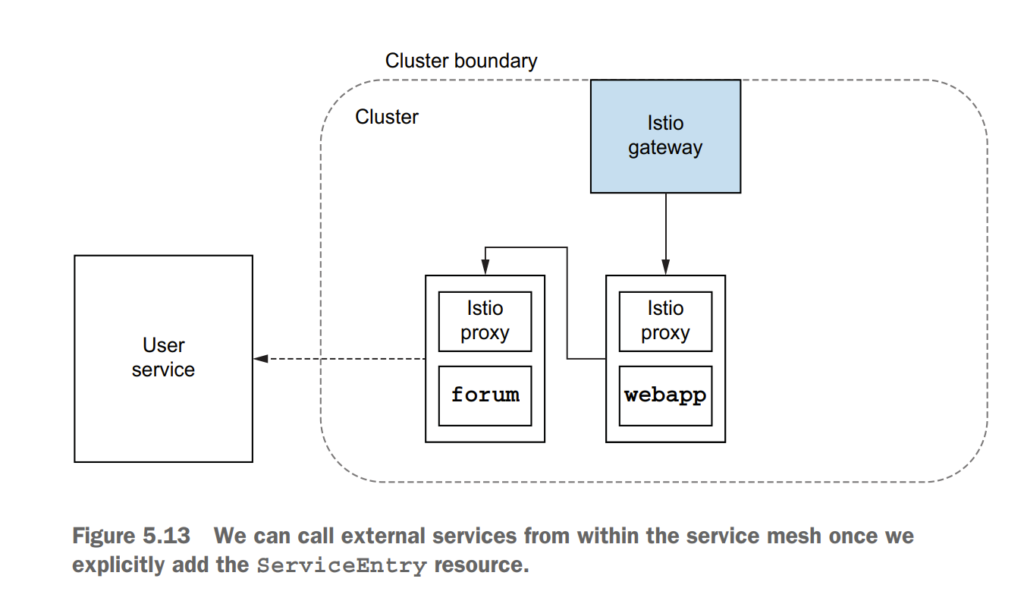
5.5 Routing to services outside your cluster by using Istio’s service discovery
In this chapter, we explored how to reduce the risk of deploying new code by using
traffic mirroring, traffic shifting, and traffic routing to slowly introduce changes to our
users.
In the next chapter, we look at making application interactions more resilient
by implementing timeouts, retries, and circuit breakers.